As a kid I fantasized about how great it would be to have a map on which you could see where you are, like the Marauders Map of Harry Potter. Who could have thought that a couple of years later there would be a technology that makes it possible, a technology so brilliant that it even takes into account Einsteins’ special theory of relativity.
Since my first GPS I am always looking for the most accurate GPS for logging my sports and hiking trips. I started in 2007 with the Garmin GPSMAP 60csx, but it was quite bulky for running (I had to keep it in hand). I therefore switched to the relatively unknown I-gotU devices. They were succeeded by the TomTom weareables (Adventurer) and they seemed pretty accurate (I still use them for open water swimming, attached to my buoy). Since they were discontinued I switched to Garmin. On my bike I have used the Edge 810, Edge 830 and am currently using the Edge 1040. For running and swimming the Fenix 7 and for hiking I recently bought the GPSMAP 67. The latter 3 are currently the top-of-the-bill consumer models from Garmin that use multiple satellite systems.
I’ve been using the Fenix 7 and Edge 1040 for quite some time now and they are giving good results and good agreement if I use them both (and I often do). I expected the GPSMAP67 to perform at least as good as them, if not better, since it has the same GPS chip, but a better antenna. So I took all three of them on a MTB trip through the forest. Auch! The result of the GPSMAP 67 was a bit disappointing: it’s track deviated from the Fenix 7 and Edge 1040 tracks. Though the Fenix and Edge are in good agreement with each other throughout the entire trip, the GPSMAP 67 showed deviations. And yes, two against one…
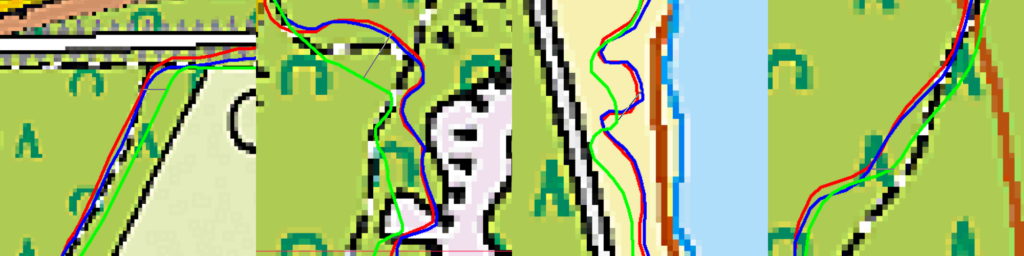
Reason to put them on the test bench for a more thorough examination…
Disclaimer: yes, I am a GPS weirdo 🤪and I go to the last cm. If you think: ‘Man, what are you fuzzing about?‘, stop reading here.
Important notice: during testing I found a serious issue on the GPSMAP 67 on which I reported in another post. Due to this issue the GPSMAP67 is unreliable because it might show your location with a large error. I reported it to Garmin Support but they don’t take it seriously and just refer to their FAQ.